VPN Protocols: Introduction and Security
Today’s Internet is a social and business platform
As we browse web pages, our personal information is collected bit-by-bit by people like advertisers and market researchers interested in knowing our likes and dislikes. They Collect information about your browser, platform, IP address, searches, browsing habits, products you buy. Based on the information they gather, they manipulate this data for their own finical gain.
Protecting your personal information is not the only concern one should have. Their are many other threats out their like viruses, malwares, trojans, spam etc, which will infiltrate your computer system if you are not careful. There are also dishonest people who hack and phish your information when your online. Protecting your online identity is so important that it becomes a job of its own.
There are many solutions to counter these security risks such as anti-viruses, anti-malware and firewalls which can protect your systems but it's a totally different thing when it comes to preventing the theft of your personal information.
Most current browsers support Private Browsing and Do Not Track options providing some solutions. However they also bring with them limitations as well. VPN, however, is one foolproof solution.
Virtual Private Network (VPN)
VPN's creates a (virtual) encrypted ‘tunnel’ between your computer and your VPN provider’s server. This tunnel ensures that the data passing through the Internet is secure from hackers and spammers. Though the technology behind VPN is complicated, the feature basically blocks people from peeking into your data, and helps protect your identity by hiding your IP address.
Using and connecting to a VPN is as easy as accessing your email account. We will go into more detail on setting up VPN clients as well as Configuring and installing VPN Server's later in the series.
PPTP
By far the most popular one, Point-to-Point Tunnelling Protocol or PPTP provides a weak 128-bit encryption but is comparatively faster than the rest because of the low encryption overhead. It supports most platforms like Windows, Mac OS X, iOS, Android, Linux, DD-WRT routers, etc. and requires no software installation as operating systems have built-in support for it.
It is easy to use and deploy, and is compatible with Dedicated IPs. It is usually the cheapest of all protocols and is the best choice for basic users who are not looking for too much security.
- Reasons to choose:
- Support array of platforms
- Easy to use
- Good support for mobile devices like Android and iOS.
- Reasons not to choose:
- Weak encryption means low security
- No support for alternate VPN port
- Easy to detect and block.
- There are paid service's out there that claim to be able to crack this encryption in 24hrs.
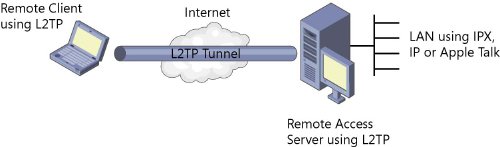
L2TP/IPSec
Layer Two Tunnelling Protocol (L2TP) uses Internet Protocol Security (IPSec) for encryption of data. It provides high 128-bit or 256-bit encryption and supports Windows, Mac OS X, Linux, iOS and Android operating systems
It also needs no software installation and is compatible with Dedicated IPs# but is preferred over PPTP because of better security. It is best for people looking for high security but can’t opt for OpenVPN for any reason.
- Reasons to choose:
- High security
- Better than PPTP
- Reasons not to choose:
- No support for alternate VPN port
OpenVPN
OpenVPN is the most secure VPN protocol and can work in places like colleges and corporate offices where other protocols are blocked. It provides secure 256-bit encryption and is usually the costliest of the protocols.
OpenVPN needs its client to be installed on the system. It is compatible with Dedicated IPs# and works on multiple ports, making it very difficult to detect and block. Thus, it is the best choice for advanced users who need high anonymity and security.
- Reasons to choose:
- High security
- Work where other protocols don’t function
- Support for alternate VPN port
- Reasons not to choose:
- Need software installation
- Works on iOS (with jail-brake and software)
- Android with difficulty (in some cases)